It’s a wrap for phase one! We have managed to keep up with the goals we set for ourselves and along with my mentor Paul Spooren we have shaken up BMX7 development all around.
Documentation Refactor
One of this phase’s goals was to understand BMX7 functionality, usage and plugins. With a lot of reading (both in-project documentation and with external sources) this was achieved and I was much more synced. While doing so I refactored some pieces of docs to help me and I found a branch I had created with some generic changes that I made in the Community Bonding phase.
These acted as inspiration and I got together a big batch of changes commited and PR’d to the bmx7 upstream.
The PR can be found here and its purpose is to achieve generic changes to ease the introduction of new developers and users to the project, as well as ease the learning curve of usage.
More info one can found in the following blogpost that describes things in detail:
It’s worth to be noted that this was not a goal per-se of the phase and that changes did take place, but they sparked other changes that are still WIP on the PR.
Testing Infrastructure
Establish the following Testing setups for testing and later on continuous integration:
- LXC running OpenWrt bridged mesh.
- Qemu OpenWrt bridged mesh networks
The idea was to establish Linux Containers and Qemu infrastructures to do testing and experimentation. Along with aparcar my mentor “we salvaged from oblivion” a very interesting and well-set project that axn had created named Mesh Linux Containers (MLC) and which takes on its own the creation, configuration and command and control (CnC) of a virtualized mesh network on a Linux host, supporting an abundance of community mesh protocols. Paul took on him the modernization of this project producing the new generation of MLC, which switches mlc’s functionalities from the shell scripting era to LXC and distrobuilder to autocreate and populate an OpenWRT mesh mother and OpenWRT clients.
On the above I also based my testing infrastructure, but being a Qubes OS user and relatively confused with LXC versions (a newb), I kept coming across issues.
The situation was able to be relaxed by investing time on QEMU for love and support (as one may find here). Again though problems like libvirt on Qubes, multiple Qemu interfaces and tricky bridging tricks on a standalone VM didn’t allow me to have the results I was hoping for.
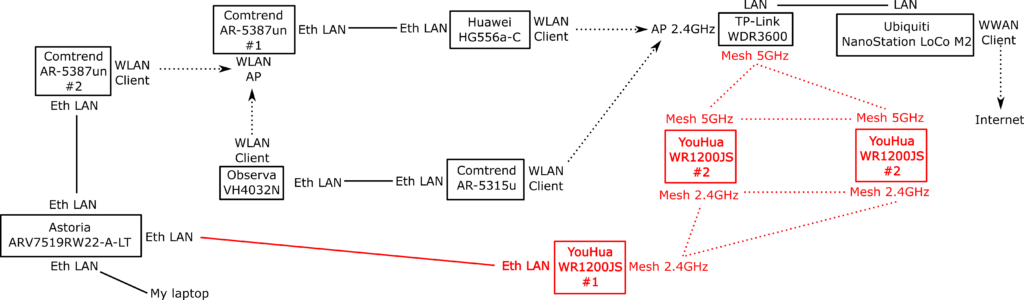
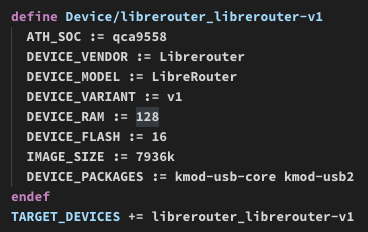
Hence, armboards were chosen. I borrowed boards from the hackerspace.gr common sharing stash of toys and I was able to interconnect a Raspberry Pi 1B, one Raspberry Pi 3B and a BeagleBone Black.
This approach is optimal for me to establish decent OpenWrt routers to test and play, that can painlessly run BMX7 (and Wireguard) and leave to the local community things to use like mesh boxes and on-the-go VPN-configured APs.
(The bmx7 luci app works like clockwork btw.)
BMX7 wg_tun Plugin
The initial goal was to implement wrapper functions to WG and establish a secure tunnel that way. This adds an overhead in the development phase, because making wg binary calls is both costly and requires to place code in places where no further improvements can be achieved.
For this reason, the embeddable wireguard implementation was chosen and we switched from addition(to the current tun src) to the creation of the wg_tun plugin earlier on than what was planned.
The idea is that adhering to the current implementation of the tunneling plugin of BMX7 we can reuse some minimum parts and establish:
- The creation of a public and a private wg key associated with the current bmx7 session (or persist across sessions).
- The advertisement of these keys and the network(IP) associated with our interface through descriptive updates for our peers to find us.
- The establishment of connections with peers that have advertised their public keys and networks (and we’ve caught them), a la tunnel announcements style.
This goal is still WIP as more testing needs to take place and optimal ways and options for bmx7 node administrators to use it. In general, for this part and until further work has been put in, the paradigm of danrl for the luci-proto-wireguard package is being followed in the sense that we want the establishment of bmx7 wg tunnel to be that easy and the static configuration or the randomized UDP ports can help get there faster.
Progress can be found on the implementation’s branch on my fork (https://github.com/luserx0/bmx7/tree/wg_tun_plugin)
Developer Misc
My dotfiles repo has seen a lot of action this first period. The refactoring of my vimrc took place to help me in reading through code (a lot of code). The configs are managed through GNU Stow. If something catches your eye, clone, run the install script, tweak and share back.
My personal Blog saw also some pretty intense developments too to make progress report sharing and tutorial posting humane. It’s based on hexo and hexo-next, it’s static and hosted on gh-pages. Perfect combo for a GSoC student. Feel free to grab it from here and use it under CC.
If you have questions on how BMX7 operates and/or is different from other mesh routing protocols feel free to post them here.
Next Steps
- Additions of features and options of the wg_plugin. Getting it merged on the upstream is a good milestone.
- Cleanup and research on reusing cryptographic and networking primitives common to Wireguard and BMX7.
- Creation of the bmx7 Debian Package.
- Port mlc functionality to mlc-ng.
- Finish the second phase of the documentation refactor.
- Attending Battemesh V12 😉
- Order hardware to play with





 “
“