In ihrer aktuellen Ausgabe 17/2019 berichtet die c’t ausführlich über das Freifunk-Projekt. Der Themenschwerpunkt umfasst insgesamt vier interessante Artikel:
Das größte Bürgernetz Deutschlands
“Freifunk: Das größte Bürgernetz Deutschlands” beschreibt das Projekt aus User-Sicht. Der Artikel erläutert, wie Freifunk-Netze technisch aufgebaut werden können und wie sich Nutzerinnen und Nutzer mit ihnen verbinden. In seinem Beitrag stellt Andrijan Möcke Freifunk einem kommerziellen Hotspot-Provider gegenüber. Jedoch übersieht er, dass es bei Freifunk nicht nur um kostenlosen Internetzugang geht sondern um viel mehr: Wir bauen gemeinsame ein freies und selbstverwaltetes Funknetzwerk, das alle Menschen in meiner Umgebung miteinander verbindet und das von niemandem einfach abgeschaltet werden kann – so Lisa im Video Freifunk verbindet.
Freifunkas bauen nicht ihr Hotspot-Netz – sie befähigen Menschen es selber zu tun: Im Kern stehen Erfahrungsaustausch und Wissensvermittlung. Gemeinsame Projekte gibt es z.B. mit der CryptoParty, Chaos macht Schule, einigen CCC-Erfas und dem Jugendnetz Berlin. Ein DIY-Ansatz ohne Hotline und Vertrag ist kaum mit Service-Anbietern vergleichbar; die Community hofft auf Engagement bei ihren Projektzielen. Die vielen Verweise auf Vereine zur Teilnahme überraschen zudem: Den mehreren hundert losen Communities stehen nur etwa 50 Vereine gegenüber.
Haftungsentspannt – Ihr Gastnetz, Freifunk und die Störerhaftung
Der Rechtsanwalt Nick Akinci gibt in seinem Beitrag “Haftungsentspannt Ihr Gastnetz, Freifunk und die Störerhaftung” eine juristische Einschätzung zum Betrieb von Freifunk Routern und offenen Funknetzen. Hierbei geht er insbesondere auf die Situation nach dem Ende der Störerhaftung für WLAN-Betreiber ein. Neben Nick Akincis liefert Reto Mantz in seinem Blog “Offene Netze und Recht” weitere Einschätzungen und Hintergründe. Reto arbeitet als Richter am Landgericht Frankfurt am Main und beschäftigte sich u.a. in seiner Dissertation mit Rechtsfragen in offenen Netzen. Seine Analyse “BGH „Dead Island“ – Wie der BGH zwar die Abschaffung der Störerhaftung (bei WLANs) bestätigt, ihr Grundübel aber weiter beibehält” gibt einen umfassenden Einblick in die derzeitige Situation bzgl. der Störerhaftung.
Einmal Hotspot, bitte!
Im dritten Artikel “Einmal Hotspot, bitte!” gibt Vincent Wiemann Kaufempfehlungen für Freifunk Router. Im direkten Vergleich stellt er fünf Geräte verschiedener Hersteller einander gegenüber. Er zeigt auf, dass ältere Geräte wie der Linksys WRT54G und der TP-Link TL-WR841N inzwischen über zu wenig Ressourcen für die immer größeren Freifunk-Netze verfügen. Getestet werden die TP-Links RE450 v1, Archer C7 v5 und Archer C50 v4 sowie die Ubiquiti AC Mesh und die AVM Fritzbox 4040. Die Empfehlung für den RE450 ist jedoch problematisch, da die Geräte der Serie zum Teil über zu wenig Arbeitsspeicher verfügen. In vielen Communities können zudem auch andere Geräte verwendet werden: Das OpenWRT-Projekt hat eine Liste mit z.B. Gluon kompatiblen Freifunk-Routern veröffentlicht.
Gemeinsam funken – Zu Besuch bei Freifunk-Communities in Stadt und Land
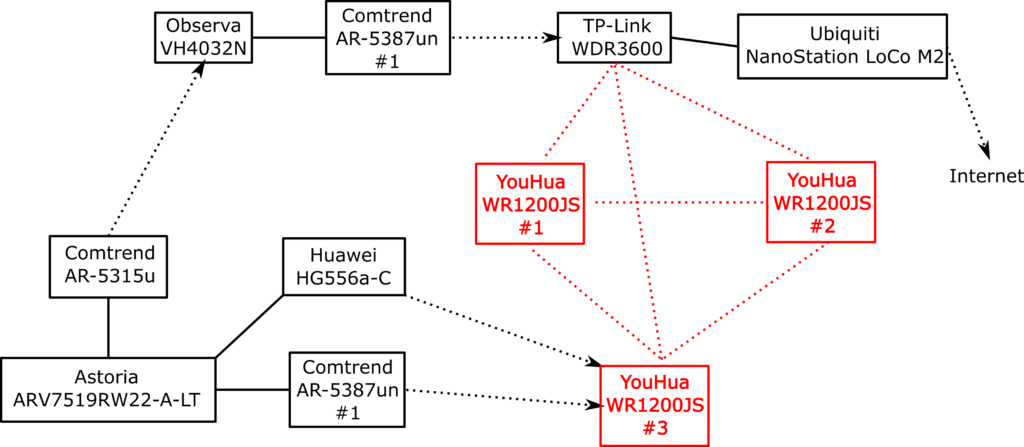
Zuletzt gibt Keywan Tonekaboni in “Gemeinsam funken – Zu Besuch bei Freifunk-Communities in Stadt und Land” einen faszinierenden Überblick über verschiedene Freifunk Communities und Projekte in Deutschland. Zu Beginn geht es zur Freifunk Community in Hanover im Hackerspace Leinelab – darauf führt die Reise zum Wireless Community Weekend, dem jährlichen Freifunk Community-Treffen in Berlin. Hier stellt Keywan Tonekaboni Gründerinnen und Gründer der Freifunk Bewegung vor. Zuletzt gibt es einen Einblick in den Netzausbau in Wittmund und das Richtfunk-Backbone an der Nordseeküste.
Insgesamt veröffentlicht der heise-Verlag ein gelungenes Bild von Freifunk, das bei vielen Interesse wecken dürfte. Vielen Dank dafür.