It has been a wild ride and this post marks the completion of GSoC 2019 for WireGuard Tunneling in BMX7. Throughout the summer a lot of effort has been put into coding, documentation and codebase restructuring; it has been a appetizer for what awaits us coming Autumn.
Overview
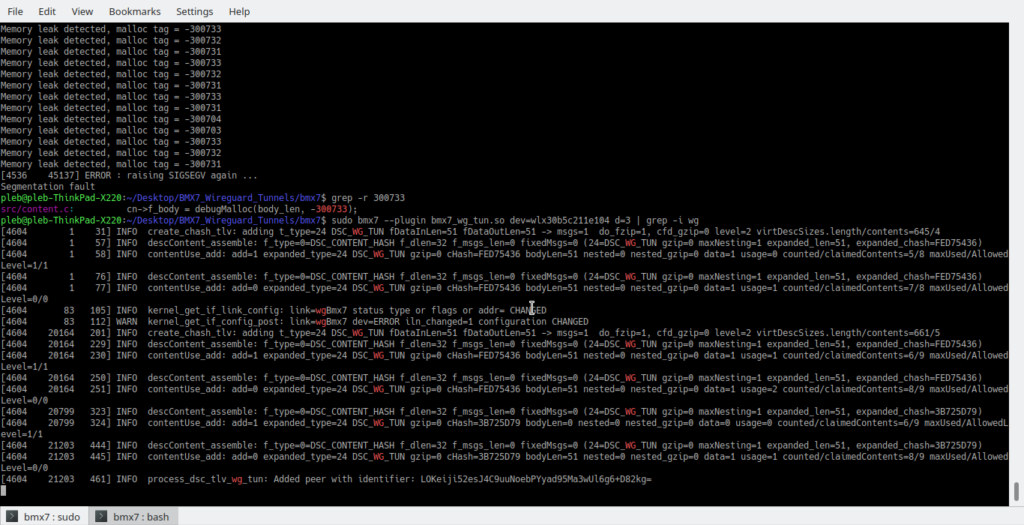
During the final phase of GSoC 2019, focus has been put into recombining what has already been done. An ideal goal had been to extend the wg_tun plugin functionality with the routing of traffic between associated peers, but this remains a work in progress. Testing has taken place and quite a few SIGSEGVs have monopolized interest. Also, research has been contacted on whether and how to cryptographic primitives used in BMX7 and WireGuard. This seems infeasible currently, due to the differences between cryptographic keys of the two.
The wg_tun Plugin
Our ultimate and prime goal has been the beta release of this plugin. The plugin offers BMX7 the capability of setting up an iproute2 WireGuard device interface with a unique pair of keys that is automatically looking for all available peers and establishes a connection with them.
In the current approach we have designed along with Axel an approach about the unique cryptographic address assigned to the wg interface (a concept similar to the existing), where the BMX7-WG auto-configured IPv6 address is a product of the unique prefix fd77::16 and the first 14 bytes of the node’s SHA224 hash. Research goes on in this to figure out the best approach (network and cryptography wise).
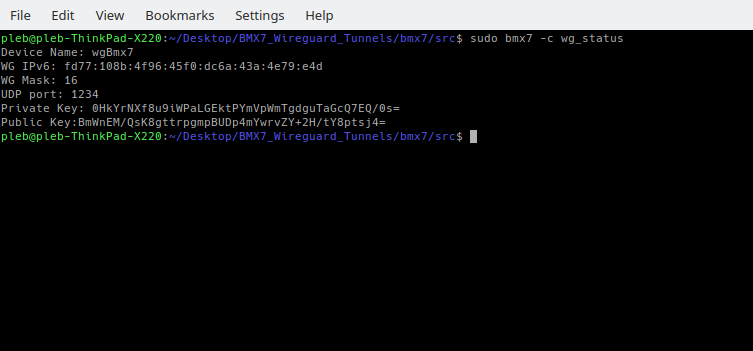
In the past days we saw the creation of wg_status option and the addition of debug flags to inform an administrator of the state of his WG device (related commit).
At this stage, testing is being performed to analyse the behaviour of the plugin after the associations among peers and include more status information and more options for the control of the plugin by the user.
The “misses”
Of course when you go too optimistic into the dark something’s gonna not work out.
In this project the misses can be summarized in: devoting more time than initially expected into studying and researching and dropping some core goals for the sake of more important ones.
The goals we “skipped” have been the Debian Package and the refactoring of Mesh Linux Containers to aid with testing.
In the studying part, I was supposed to devote only the community bonding period and part of the first phase to study white paper and get up to speed with theory between what needed be implemented and fiddled. I ended up devoting time throughout all the phases, but I’m happy with what I’ve learned.
Further Work
The intention to continue work on BMX7 is trivial to answer. GSoC has been a good experience and way to get started with the codebase of BMX7, but free flowing, detrimental work is scheduled for after it.
- Add command line functionality for the wg_tun plugin, include it along with the Refactor of command line arguments issue,
- Add more developer documentation for BMX7 newcomers, like Plugin Creation and Glossary,
- Create the bmx7 Debian package (check here),
- Rework mlc into mlc-ng (as reported here).
Final Thoughts
I’m very happy I got the chance to help Freifunk’s goals and hope to continue however I can.
Battlmesh V12 was super nice and I look forward to next year’s (I hope it’s Netherlands).
At last, I would like to thank my mentors Paul Spooren and Axel Neumann for their advice and way they approach cooperation.