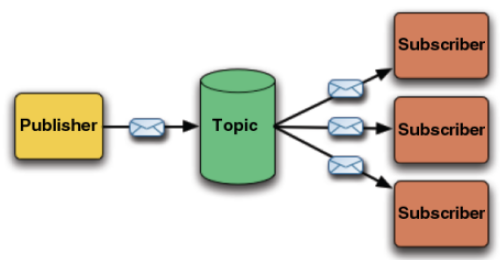
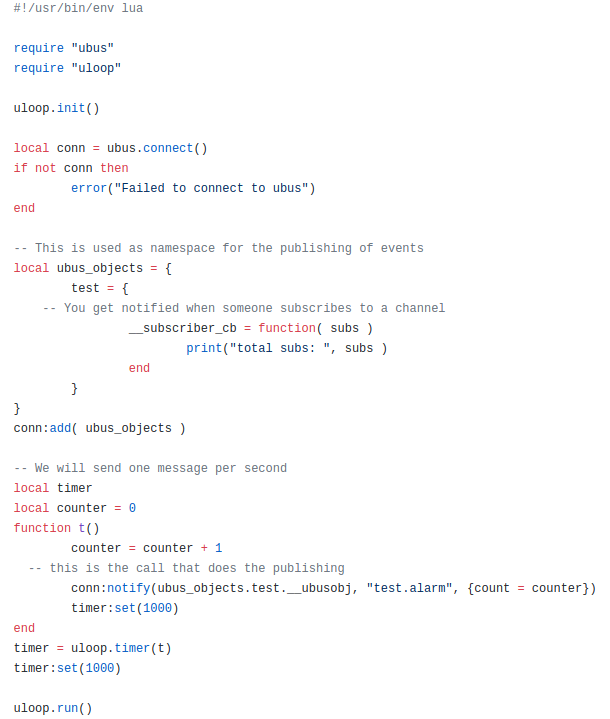
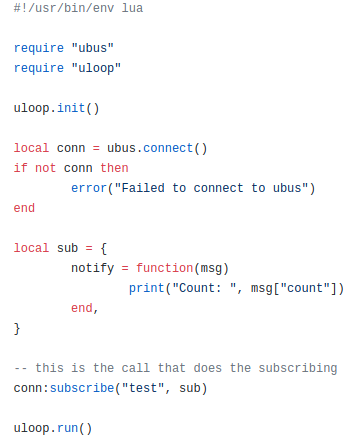
I’ve been strugling with the workflow of the development.
The development workflow has a lot of shortcomings:
- depends on hardware features (like a radio)
- the platform where it runs is an embedded operating system, so you need one to test
- the architecture is not the same as my development computer, so running the same code in my computer is difficult (don’t have ubus, libc is different)
If I solve this, the solution can be used to better do Continuous Integration by testing code on a comparable platform.
So I started looking for a way to work easier.
These are my requiremnets:
Must:
- openwrt machine (could be VM)
- be able to run recently coded code
Desirable:
- virtual machine
- rapid turnaround time
So, this are the options that I found:
Portable OpenWRT devices (MR3020)
Use this with an ethernet cable and ethernet card, connect to it through ssh and sync code with device.
On the router:
opkg install openssh-sftp-server
On the pc:
sudo apt install sshfs
sshfs root@192.168.1.1:/root/testcode testcode
In order to umount the directory:
fusermount -u testcode
This allows to have a native platform, all the hardware features, but has the downside of having to have a device connected to the computer.
Virtual Machine
This way of calling qemu lets me have a local virtual machine, but does not have access to the network:
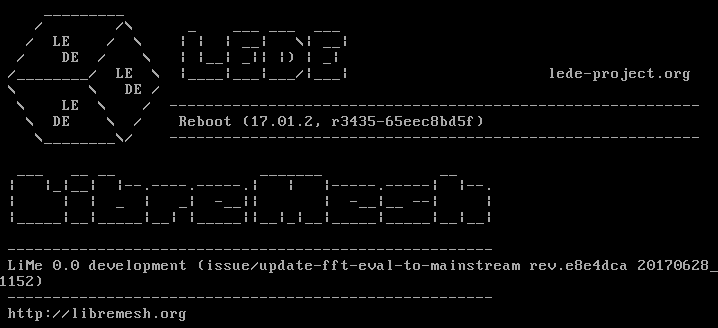
qemu-system-x86_64 -nographic -M q35 -drive file=output/x86/generic/Default/lime_default/lede-17.01.2-libremesh-x86-generic-combined-ext4.img,id=d0,if=none,bus=0,unit=0 -device ide-hd,drive=d0,bus=ide.0
I was able to connect to the network using virt-manager… and from there I got this long call to qemu:
qemu-system-x86_64 \
-enable-kvm \
-name guest=generic,debug-threads=on \
-S \
-object secret,id=masterKey0,format=raw,file=/var/lib/libvirt/qemu/domain-5-generic/master-key.aes \
-machine pc-i440fx-yakkety,accel=kvm,usb=off \
-cpu Broadwell-noTSX \
-m 1024 \
-realtime mlock=off \
-smp 1,sockets=1,cores=1,threads=1 \
-uuid 062afe50-1e83-4c7a-a16a-e3078d53dd63 \
-no-user-config \
-nodefaults \
-chardev socket,id=charmonitor,path=/var/lib/libvirt/qemu/domain-5-generic/monitor.sock,server,nowait \
-mon chardev=charmonitor,id=monitor,mode=control \
-rtc base=utc,driftfix=slew \
-global kvm-pit.lost_tick_policy=discard \
-no-hpet \
-no-shutdown \
-global PIIX4_PM.disable_s3=1 \
-global PIIX4_PM.disable_s4=1 \
-boot strict=on \
-device ich9-usb-ehci1,id=usb,bus=pci.0,addr=0x6.0x7 \
-device ich9-usb-uhci1,masterbus=usb.0,firstport=0,bus=pci.0,multifunction=on,addr=0x6 \
-device ich9-usb-uhci2,masterbus=usb.0,firstport=2,bus=pci.0,addr=0x6.0x1 \
-device ich9-usb-uhci3,masterbus=usb.0,firstport=4,bus=pci.0,addr=0x6.0x2 \
-device virtio-serial-pci,id=virtio-serial0,bus=pci.0,addr=0x5 \
-drive file=/home/nicopace/projects/redlibre/altermundi/librestack/lime-sdk/output/x86/generic/Generic/lime_default/lede-17.01.2-libremesh-x86-generic-combined-ext4.img,format=raw,if=none,id=drive-ide0-0-1 \
-device ide-hd,bus=ide.0,unit=1,drive=drive-ide0-0-1,id=ide0-0-1,bootindex=1 \
-netdev tap,fd=26,id=hostnet0 \
-device e1000,netdev=hostnet0,id=net0,mac=52:54:00:86:34:95,bus=pci.0,addr=0x3 \
-netdev tap,fd=28,id=hostnet1 \
-device e1000,netdev=hostnet1,id=net1,mac=52:54:00:86:8b:58,bus=pci.0,addr=0x8 \
-chardev pty,id=charserial0 \
-device isa-serial,chardev=charserial0,id=serial0 \
-chardev spicevmc,id=charchannel0,name=vdagent \
-device virtserialport,bus=virtio-serial0.0,nr=1,chardev=charchannel0,id=channel0,name=com.redhat.spice.0 \
-spice port=5900,addr=127.0.0.1,disable-ticketing,image-compression=off,seamless-migration=on \
-device qxl-vga,id=video0,ram_size=67108864,vram_size=67108864,vram64_size_mb=0,vgamem_mb=16,max_outputs=1,bus=pci.0,addr=0x2 \
-device intel-hda,id=sound0,bus=pci.0,addr=0x4 \
-device hda-duplex,id=sound0-codec0,bus=sound0.0,cad=0 \
-chardev spicevmc,id=charredir0,name=usbredir \
-device usb-redir,chardev=charredir0,id=redir0,bus=usb.0,port=1 \
-chardev spicevmc,id=charredir1,name=usbredir \
-device usb-redir,chardev=charredir1,id=redir1,bus=usb.0,port=2 \
-device virtio-balloon-pci,id=balloon0,bus=pci.0,addr=0x7 \
-msg timestamp=on
I need to distill the relevant information from there.
With that last config and using an ui option in virt-manager, I was able to access the usb device TP-Link TL_WN822Nv1 on the Virtual Machine, but I was not able to use it yet because of driver problems.
Have to keep digging into that.
If you have any idea on how to do this better, please write in the comments.

 .
.